A Chinese technology firm has been siphoning text messages and call
records from cheap Android-based mobile smart phones and secretly
sending the data to servers in China, researchers revealed this week.
The revelations came the same day the White House and the U.S. Department of Homeland Security
issued sweeping guidelines aimed at building security into
Internet-connected devices, and just hours before a key congressional
panel sought recommendations from industry in regulating basic security
standards for so-called “Internet of Things” (IoT) devices.
At the center of the spyware controversy is software made by Shanghai ADUPS Technology, a Chinese firm whose product touts the ability to wirelessly update software installed on mobile and and IoT devices. The ADUPS technology is typically bundled with smart phones made by dozens of global wireless firms including ZTE, BLU and Huawei, and sold at popular consumer destinations like Amazon and BestBuy. Often retailing for between $50 and $100, the sleek and powerful devices sell so cheaply because they also require the user to accept on-screen advertisements.
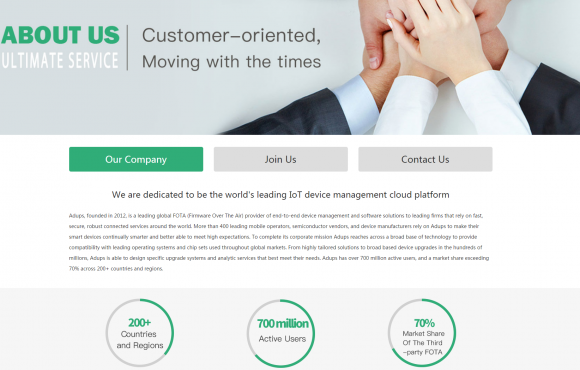 An About Us page at ADUPS’s Web site explains the company’s foothold in the IoT market.
An About Us page at ADUPS’s Web site explains the company’s foothold in the IoT market.
According to research released this week, the low up-front cost of these smart phones may be subsidized not just by ads but by also by the theft of private information stolen from users. Researchers at Fairfax, Va.-based security firm Kryptowire say the ADUPS software gives the company near-total control over the devices that it runs on, and that they have proof ADUPS has abused that control to siphon personal data from countless consumers.
Kryptowire researchers say they stumbled upon ADUPS’s spyware capabilities by accident after purchasing a $59 BLU R1 HD smart phone from Amazon.com for use during international travel. Prying apart the phone and the ADUPS software, they discovered that all call records and text messages to and from the device were being digitally copied, encrypted and secretly forwarded to a server in Shanghai, China every 72 hours.
They also learned that ADUPS’s product was able to mine user text messages for specific strings of text, as well as install and remove any software from host devices.
“This behavior cannot be detected by mobile anti-virus tools because they assume that software that ships with the device is not malware and that it is white-listed,” Kryptowire wrote in an advisory published Tuesday. “We were able to capture, decrypt, and trace the data on the network as they were sent to multiple server locations that are located in Shanghai, China.”
In a statement posted to its Web site, ADUPS said it collects “model information, device status, application information, bin/xbin information and summary information from phones and messages,” and that it has done so “in response to user demand to screen out junk texts and calls from advertisers.”
ADUPS further claims that the functionality was added in June 2016 to some Blu Product Inc. devices, and that it has since shipped an update through its firmware updating software to disable the spying functionality on Blu phones.
But Azzedine Benameur, director of research at Kryptowire, said ADUPS’s software — deeply embedded alongside the operating system on these mobile devices — gives it full ability to re-enable the spyware capabilities at any time. He says ADUPS’s public response to their research raises more questions than it answers.
“They do not provide how many devices were affected and how the data were used,” Benameur said. “Also, they don’t mention who had access to that data, including third parties and the Chinese government. Also, there might be other [manufacturers] and device models affected that ADUPS does not mention.”
ADUPS claims on its Web site to have worldwide presence with more than 700 million active users, and that its firmware is integrated into “more than 400 leading mobile operators, semiconductor vendors and device manufacturers spanning from wearable and mobile devices to cars and televisions.”
“This is just one random device of theirs that we looked at,” Benameur said. “For a company that claims to provide over-the-air updates for 700 million devices, including cars and millions of IoT devices…this is really scary and unacceptable behavior.”
 ADUPS’s offer to business partners, circa January 2015.
ADUPS’s offer to business partners, circa January 2015.
ADUPS’s current site promises the company’s partners “big data analytics” and higher profit for partners. Earlier versions of the same page from 2015 and cached at the Internet Archive promise partners a slightly less euphemistic menu of services, from an “app push service,” and “device data mining” to “unique package checking” and “mobile advertising.” Interestingly, this story from January 2015 documents how ADUPS’s software has been used to install unwanted apps on customer mobile devices.
As for the Blu R1 HD phone? Benameur said it would be nice if it came with a disclosure that owners can expect zero privacy or control while using it. Aside from that? “At $59, it’s a steal,” Benameur said. “Minus the spyware, it’s a great phone.”
Two of those attacks — an hours-long digital siege in October against Internet infrastructure provider Dyn, and a September attack that crippled KrebsOnSecurity for days — harnessed the computing power and network bandwidth of hundreds of thousands of Internet-based cameras and DVRs that were secured with the same default password and configured to be remotely controllable over the Web. A Chinese manufacturing firm whose electronics featured prominently in many of the IoT devices used in those attacks recently said it was issuing a recall for millions of the vulnerable devices — which were shipped with user credentials that were hard-coded into the devices and that could not be easily changed by users.
Both the attack on Dyn and against this site were referenced on multiple occasions today by lawmakers and witnesses to a U.S. House Energy & Commerce Committee hearing titled “Understanding the Role of Connected Devices in Recent Cyber Attacks.”
Bruce Schneier, a security expert who has long advocated holding software vendors legally liable for producing fundamentally flawed and/or insecure products, said the IoT attacks and this latest scandal with ADUPS are examples of a market failure that is crying out for government regulation.
“In many ways, the Dyn attack was benign,” Schneier said in his written testimony. “Some websites went offline for a while. No one was killed. No property was destroyed. But computers have permeated our lives. The Internet now affects the world in a direct physical manner. The Internet of Things is bringing computerization and connectivity to many tens of millions of devices worldwide. We are connecting cars, drones, medical devices, and home thermostats. What was once benign is now dangerous.”
Schneier encouraged lawmakers to think about commercial software and hardware that gets shipped with junk security as a form of pollution: But instead of pumping liquid toxic waste into thinly-lined man-made cesspools, many makers of low-end electronics are churning out default-insecure products that will likely remain in operation — and therefore a public nuisance — for many years to come.
“We’re asking consumers to shore up lousy products,” Schneier told the committee. “It shouldn’t be that there are default passwords. These devices are low profit margin, they’re made offshore. And the buyer and seller don’t care. I might own this DVR, you might own it. You don’t know if it’s secure or not. You can’t test it. And you fundamentally don’t care. You bought it for the features and the price.”
Rep. Anna Eshoo (D-Calif.) called attention to a bill she’s offered — the Promoting Good Cyber Hygiene Act of 2015 — that calls on government regulators to develop best practices aimed at boosting public and private sector network security. As noted above, the White House and the Department of Homeland Security both did just that on Tuesday, each issuing guidelines on cybersecurity for IoT devices.
“We need a good housekeeping seal of approval on this, and my bill called for NIST [the National Institute of Standards and Technology] to set the standards — not Congress — because we really don’t know anything about that, and when we miss the mark we miss it by a wide mile,” Eshoo said.
Indeed, some experts have advocated creating a sort of government-approved Underwriters Laboratories for cybersecurity that would perhaps imprint its seal of approval on certified IoT devices. But Schneier said most consumers are unlikely to be moved by “a sticker that says this device costs $20 more and is 30 percent less likely to annoy people you don’t know.”
Instead, he suggested Congress should create a new federal agency to regulate basic secure design standards for IoT devices. “A U.S.-only regulatory system will affect the products in the rest of the world because this is software,” Schneier said. “Companies will make one software and sell it everywhere. It makes no sense for anyone to come up with two versions of their software.”
 Bruce Schneier, left, and Kevin Fu.
Bruce Schneier, left, and Kevin Fu.
Rep. Eshoo called the prospect of creating new bureaucracy in a Republican controlled Congress and White House an idea that was “dead in the water.”
“We have a continuing new, new majority and I don’t think they want to create a new agency,” Eshoo said. “They don’t like stuff like that. New agencies, new regulations, we’re dead in the water. But we can’t leave this issue dead in the water. Our country deserves better.”
If this Congress or the next is reluctant to mandate basic cybersecurity standards for IoT devices, they may soon find themselves forced to legislate in a hurry when people start dying because of IoT insecurity, Schneier said.
“The government is getting involved here regardless,” he said. “The risks are too great and stakes are too high, and nothing motivates government into action [more] than security and fear. In 2001, we had another small-government, no-regulation administration produce a new federal agency 44 days after the terrorist attacks. If something similar happens with the Internet of Things, we’re going to have a similar response. I see the choice here not between government involvement and no government involvement, but between smart government and stupid government. This is the world of dangerous things, and we regulate dangerous things.”
Emphasizing that point, Kevin Fu, chief executive at healthcare security provider Virta Laboratories, told the panel that healthcare and medical device community dodged a bullet on the Dyn attack.
“Hospitals survived not by design, but by luck. The adversary did not target healthcare. This time,” Fu said in his written testimony (PDF). “Dyn represents a single point of failure for resolving Internet names, but hospitals have other kinds of single points of failure. For instance, heating and ventilation now resembles IoT with unpatched computers controlling negative pressure in units with highly infectious diseases.”
Such attacks, he said, have very quickly moved from the theoretical to real life. Earlier this month, a denial-of-service attack like the one that knocked my site and Dyn offline was reportedly used to shut off environmental controls at two apartment buildings in Finland, temporarily leaving residents there without heat or hot water for several days. Also this month, a hospital in the United Kingdom was forced to cancel surgeries and divert trauma patients to nearby hospitals after a cyberattack shut down its internal systems.
Fu urged Congress to study the feasibility of standing up an independent, national embedded cybersecurity testing facility modeled after the automotive crash testing conducted by the National Transportation Safety Board (NTSB). Such a center, he posited, could serve as a security test-bed for everything from consumer IoT devices to far more sensitive medical equipment and embedded health and safety devices, more of which are being connected to the Internet each day.
“The Mayo Clinic reportedly spends roughly $300K per medical device to perform security assessment, and they have thousands of models of devices,” Fu explained. “It makes little economic sense to have individual hospitals testing the security of devices that ought to remain secure for all 6,000 hospitals in the USA. Cybersecurity ought to be a public good much like automobile safety. Imagine if every car dealer were individually responsible for crash testing automobiles: costs would skyrocket and the public would have little confidence. A facility for embedded cybersecurity at the scale of a hospital could provide testing to both government and industry, while allowing students to conduct innovative research during surplus time.”
Fu also suggested that the government could do a much better job working with industry partners to encourage more people to pursue careers in cybersecurity.
“There are tens of thousands of unfilled cybersecurity jobs in the USA,” Fu said. “Existing approaches aren’t insufficient to train a large enough work force to counter growing cybersecurity threats against IoT devices, our economy, and infrastructure.”
Whether or not Congress tries to improve IoT security, miscreants who leverage poor IoT security for criminal purposes will continue their search for additional systems that can be rented out in denial-of-service attacks or used in high-stakes digital shakedowns for money, said Dale Drew, chief security officer at Level 3 Communications.
“Bad actors are increasingly attracted to IoT devices since they can use those devices without being detected for long periods of time, they know most devices will not be monitored or updated, and they know there are no endpoint protection capabilities on IoT devices that can detect and remove the threats,” Drew said. “Network operators, device manufacturers and users will need to remain vigilant to the security risks these devices present.”
Source: https://krebsonsecurity.com/2016/11/chinese-iot-firm-siphoned-text-messages-call-records/
At the center of the spyware controversy is software made by Shanghai ADUPS Technology, a Chinese firm whose product touts the ability to wirelessly update software installed on mobile and and IoT devices. The ADUPS technology is typically bundled with smart phones made by dozens of global wireless firms including ZTE, BLU and Huawei, and sold at popular consumer destinations like Amazon and BestBuy. Often retailing for between $50 and $100, the sleek and powerful devices sell so cheaply because they also require the user to accept on-screen advertisements.

According to research released this week, the low up-front cost of these smart phones may be subsidized not just by ads but by also by the theft of private information stolen from users. Researchers at Fairfax, Va.-based security firm Kryptowire say the ADUPS software gives the company near-total control over the devices that it runs on, and that they have proof ADUPS has abused that control to siphon personal data from countless consumers.
Kryptowire researchers say they stumbled upon ADUPS’s spyware capabilities by accident after purchasing a $59 BLU R1 HD smart phone from Amazon.com for use during international travel. Prying apart the phone and the ADUPS software, they discovered that all call records and text messages to and from the device were being digitally copied, encrypted and secretly forwarded to a server in Shanghai, China every 72 hours.
They also learned that ADUPS’s product was able to mine user text messages for specific strings of text, as well as install and remove any software from host devices.
“This behavior cannot be detected by mobile anti-virus tools because they assume that software that ships with the device is not malware and that it is white-listed,” Kryptowire wrote in an advisory published Tuesday. “We were able to capture, decrypt, and trace the data on the network as they were sent to multiple server locations that are located in Shanghai, China.”
In a statement posted to its Web site, ADUPS said it collects “model information, device status, application information, bin/xbin information and summary information from phones and messages,” and that it has done so “in response to user demand to screen out junk texts and calls from advertisers.”
ADUPS further claims that the functionality was added in June 2016 to some Blu Product Inc. devices, and that it has since shipped an update through its firmware updating software to disable the spying functionality on Blu phones.
But Azzedine Benameur, director of research at Kryptowire, said ADUPS’s software — deeply embedded alongside the operating system on these mobile devices — gives it full ability to re-enable the spyware capabilities at any time. He says ADUPS’s public response to their research raises more questions than it answers.
“They do not provide how many devices were affected and how the data were used,” Benameur said. “Also, they don’t mention who had access to that data, including third parties and the Chinese government. Also, there might be other [manufacturers] and device models affected that ADUPS does not mention.”
ADUPS claims on its Web site to have worldwide presence with more than 700 million active users, and that its firmware is integrated into “more than 400 leading mobile operators, semiconductor vendors and device manufacturers spanning from wearable and mobile devices to cars and televisions.”
“This is just one random device of theirs that we looked at,” Benameur said. “For a company that claims to provide over-the-air updates for 700 million devices, including cars and millions of IoT devices…this is really scary and unacceptable behavior.”

ADUPS’s current site promises the company’s partners “big data analytics” and higher profit for partners. Earlier versions of the same page from 2015 and cached at the Internet Archive promise partners a slightly less euphemistic menu of services, from an “app push service,” and “device data mining” to “unique package checking” and “mobile advertising.” Interestingly, this story from January 2015 documents how ADUPS’s software has been used to install unwanted apps on customer mobile devices.
As for the Blu R1 HD phone? Benameur said it would be nice if it came with a disclosure that owners can expect zero privacy or control while using it. Aside from that? “At $59, it’s a steal,” Benameur said. “Minus the spyware, it’s a great phone.”
NEW IOT REGULATIONS?
The ADUPS scandal, first reported by The New York Times, comes as U.S. lawmakers are under increasing pressure to legislate basic software security standards for Internet-connected devices. Many low-cost IoT devices — from consumer routers to security cameras and digital video recorders (DVRs) — ship with little to no security built in. This has left millions of consumer devices ripe for exploitation by malicious hackers who enslave the devices in powerful cyber attacks designed to knock Web sites offline and otherwise disrupt Internet services.Two of those attacks — an hours-long digital siege in October against Internet infrastructure provider Dyn, and a September attack that crippled KrebsOnSecurity for days — harnessed the computing power and network bandwidth of hundreds of thousands of Internet-based cameras and DVRs that were secured with the same default password and configured to be remotely controllable over the Web. A Chinese manufacturing firm whose electronics featured prominently in many of the IoT devices used in those attacks recently said it was issuing a recall for millions of the vulnerable devices — which were shipped with user credentials that were hard-coded into the devices and that could not be easily changed by users.
Both the attack on Dyn and against this site were referenced on multiple occasions today by lawmakers and witnesses to a U.S. House Energy & Commerce Committee hearing titled “Understanding the Role of Connected Devices in Recent Cyber Attacks.”
Bruce Schneier, a security expert who has long advocated holding software vendors legally liable for producing fundamentally flawed and/or insecure products, said the IoT attacks and this latest scandal with ADUPS are examples of a market failure that is crying out for government regulation.
“In many ways, the Dyn attack was benign,” Schneier said in his written testimony. “Some websites went offline for a while. No one was killed. No property was destroyed. But computers have permeated our lives. The Internet now affects the world in a direct physical manner. The Internet of Things is bringing computerization and connectivity to many tens of millions of devices worldwide. We are connecting cars, drones, medical devices, and home thermostats. What was once benign is now dangerous.”
Schneier encouraged lawmakers to think about commercial software and hardware that gets shipped with junk security as a form of pollution: But instead of pumping liquid toxic waste into thinly-lined man-made cesspools, many makers of low-end electronics are churning out default-insecure products that will likely remain in operation — and therefore a public nuisance — for many years to come.
“We’re asking consumers to shore up lousy products,” Schneier told the committee. “It shouldn’t be that there are default passwords. These devices are low profit margin, they’re made offshore. And the buyer and seller don’t care. I might own this DVR, you might own it. You don’t know if it’s secure or not. You can’t test it. And you fundamentally don’t care. You bought it for the features and the price.”
Rep. Anna Eshoo (D-Calif.) called attention to a bill she’s offered — the Promoting Good Cyber Hygiene Act of 2015 — that calls on government regulators to develop best practices aimed at boosting public and private sector network security. As noted above, the White House and the Department of Homeland Security both did just that on Tuesday, each issuing guidelines on cybersecurity for IoT devices.
“We need a good housekeeping seal of approval on this, and my bill called for NIST [the National Institute of Standards and Technology] to set the standards — not Congress — because we really don’t know anything about that, and when we miss the mark we miss it by a wide mile,” Eshoo said.
Indeed, some experts have advocated creating a sort of government-approved Underwriters Laboratories for cybersecurity that would perhaps imprint its seal of approval on certified IoT devices. But Schneier said most consumers are unlikely to be moved by “a sticker that says this device costs $20 more and is 30 percent less likely to annoy people you don’t know.”
Instead, he suggested Congress should create a new federal agency to regulate basic secure design standards for IoT devices. “A U.S.-only regulatory system will affect the products in the rest of the world because this is software,” Schneier said. “Companies will make one software and sell it everywhere. It makes no sense for anyone to come up with two versions of their software.”

Rep. Eshoo called the prospect of creating new bureaucracy in a Republican controlled Congress and White House an idea that was “dead in the water.”
“We have a continuing new, new majority and I don’t think they want to create a new agency,” Eshoo said. “They don’t like stuff like that. New agencies, new regulations, we’re dead in the water. But we can’t leave this issue dead in the water. Our country deserves better.”
If this Congress or the next is reluctant to mandate basic cybersecurity standards for IoT devices, they may soon find themselves forced to legislate in a hurry when people start dying because of IoT insecurity, Schneier said.
“The government is getting involved here regardless,” he said. “The risks are too great and stakes are too high, and nothing motivates government into action [more] than security and fear. In 2001, we had another small-government, no-regulation administration produce a new federal agency 44 days after the terrorist attacks. If something similar happens with the Internet of Things, we’re going to have a similar response. I see the choice here not between government involvement and no government involvement, but between smart government and stupid government. This is the world of dangerous things, and we regulate dangerous things.”
Emphasizing that point, Kevin Fu, chief executive at healthcare security provider Virta Laboratories, told the panel that healthcare and medical device community dodged a bullet on the Dyn attack.
“Hospitals survived not by design, but by luck. The adversary did not target healthcare. This time,” Fu said in his written testimony (PDF). “Dyn represents a single point of failure for resolving Internet names, but hospitals have other kinds of single points of failure. For instance, heating and ventilation now resembles IoT with unpatched computers controlling negative pressure in units with highly infectious diseases.”
Such attacks, he said, have very quickly moved from the theoretical to real life. Earlier this month, a denial-of-service attack like the one that knocked my site and Dyn offline was reportedly used to shut off environmental controls at two apartment buildings in Finland, temporarily leaving residents there without heat or hot water for several days. Also this month, a hospital in the United Kingdom was forced to cancel surgeries and divert trauma patients to nearby hospitals after a cyberattack shut down its internal systems.
Fu urged Congress to study the feasibility of standing up an independent, national embedded cybersecurity testing facility modeled after the automotive crash testing conducted by the National Transportation Safety Board (NTSB). Such a center, he posited, could serve as a security test-bed for everything from consumer IoT devices to far more sensitive medical equipment and embedded health and safety devices, more of which are being connected to the Internet each day.
“The Mayo Clinic reportedly spends roughly $300K per medical device to perform security assessment, and they have thousands of models of devices,” Fu explained. “It makes little economic sense to have individual hospitals testing the security of devices that ought to remain secure for all 6,000 hospitals in the USA. Cybersecurity ought to be a public good much like automobile safety. Imagine if every car dealer were individually responsible for crash testing automobiles: costs would skyrocket and the public would have little confidence. A facility for embedded cybersecurity at the scale of a hospital could provide testing to both government and industry, while allowing students to conduct innovative research during surplus time.”
Fu also suggested that the government could do a much better job working with industry partners to encourage more people to pursue careers in cybersecurity.
“There are tens of thousands of unfilled cybersecurity jobs in the USA,” Fu said. “Existing approaches aren’t insufficient to train a large enough work force to counter growing cybersecurity threats against IoT devices, our economy, and infrastructure.”
Whether or not Congress tries to improve IoT security, miscreants who leverage poor IoT security for criminal purposes will continue their search for additional systems that can be rented out in denial-of-service attacks or used in high-stakes digital shakedowns for money, said Dale Drew, chief security officer at Level 3 Communications.
“Bad actors are increasingly attracted to IoT devices since they can use those devices without being detected for long periods of time, they know most devices will not be monitored or updated, and they know there are no endpoint protection capabilities on IoT devices that can detect and remove the threats,” Drew said. “Network operators, device manufacturers and users will need to remain vigilant to the security risks these devices present.”
Source: https://krebsonsecurity.com/2016/11/chinese-iot-firm-siphoned-text-messages-call-records/