In what’s being billed as an unprecedented global law enforcement
response to cybercrime, federal investigators in the United States,
United Kingdom and Europe today say they’ve dismantled a sprawling
cybercrime machine known as “Avalanche” — a distributed, cloud-hosting
network that for the past seven years has been rented out to fraudsters
for use in launching countless malware and phishing attacks.
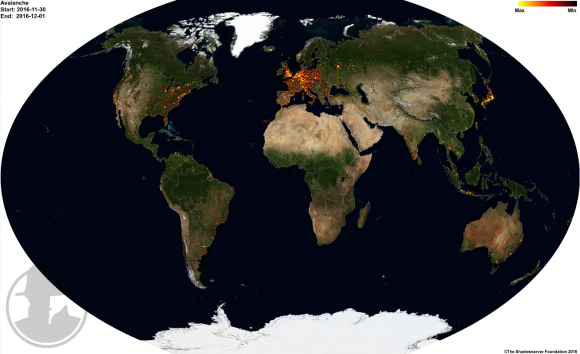 The global distribution of servers used in the Avalanche crime machine. Source: Shadowserver.org
The global distribution of servers used in the Avalanche crime machine. Source: Shadowserver.org
According to Europol, the action was the result of a four-year joint investigation between Europol, Eurojust the FBI and authorities in the U.K. and Germany that culminated on Nov. 30, 2016 with the arrest of five individuals, the seizure of 39 Web servers, and the sidelining of more than 830,000 web domains used in the scheme.
Built as a criminal cloud-hosting environment that was rented out to scammers, spammers other ne’er-do-wells, Avalanche has been a major source of cybercrime for years. In 2009, when investigators say the fraud network first opened for business, Avalanche was responsible for funneling roughly two-thirds of all phishing attacks aimed at stealing usernames and passwords for bank and e-commerce sites. By 2011, Avalanche was being heavily used by crooks to deploy banking Trojans.
The U.K.’s National Crime Agency (NCA), says the more recent Avalanche fraud network comprised up to 600 servers worldwide and was used to host as many as 800,000 web domains at a time.
“Cyber criminals rented the servers and through them launched and managed digital fraud campaigns, sending emails in bulk to infect computers with malware, ransomware and other malicious software that would steal users’ bank details and other personal data,” the NCA said in a statement released today on the takedown. The criminals used the stolen information for fraud or extortion. At its peak 17 different types of malware were hosted by the network, including major strains with names such as goznym, urlzone, pandabanker and loosemailsniffer.At least 500,000 computers around the world were infected and controlled by the Avalanche system on any given day.”
The Avalanche network was especially resilient because it relied on a hosting method known as fast-flux, a kind of round-robin technique that lets botnets hide phishing and malware delivery sites behind an ever-changing network of compromised systems acting as proxies.
“The complex setup of the Avalanche network was popular amongst cybercriminals, because of the double fast flux technique offering enhanced resilience to takedowns and law enforcement action,” Europol said in its statement.
It’s worth noting here that Avalanche has for many years been heavily favored by crime gangs to deploy Zeus and SpyEye malware variants involved in cleaning out bank accounts for a large number of small to mid-sized businesses. These attacks relied heavily on so-called “money mules,” people willingly or unwittingly recruited into helping fraudsters launder stolen funds.
At the time of the takedown, the Avalanche cybercrime infrastructure spanned more than 180 countries, according to The Shadowserver Foundation, a nonprofit group that helped authorities gain control over the Avalanche domains. Read more on Shadowserver’s role in this effort here.
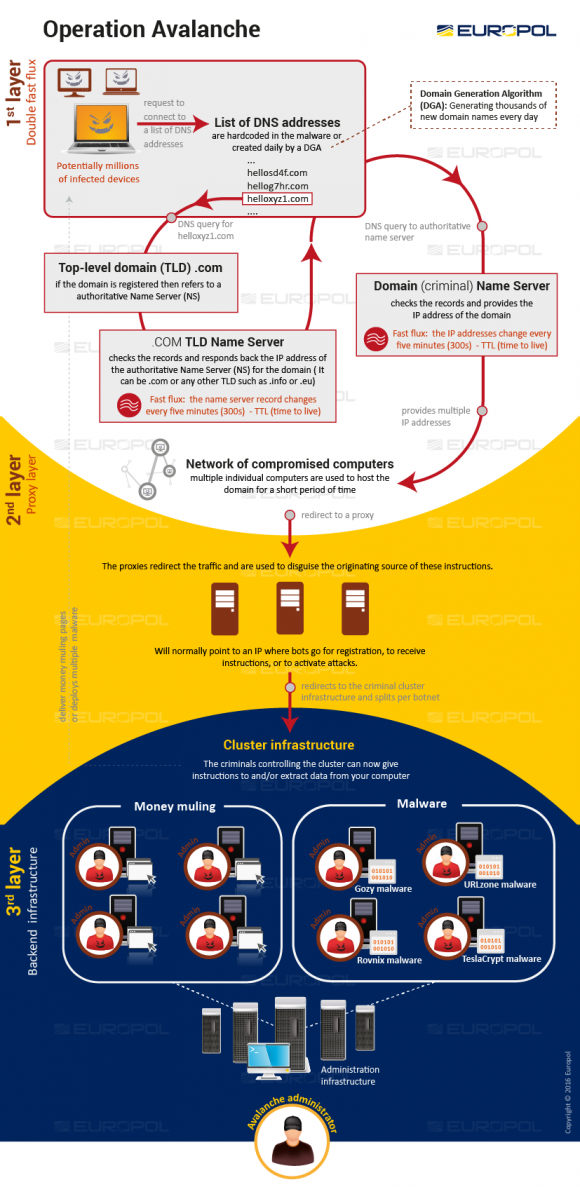 The Avalanche crime infrastructure. Image: Europol
The Avalanche crime infrastructure. Image: Europol
Source

According to Europol, the action was the result of a four-year joint investigation between Europol, Eurojust the FBI and authorities in the U.K. and Germany that culminated on Nov. 30, 2016 with the arrest of five individuals, the seizure of 39 Web servers, and the sidelining of more than 830,000 web domains used in the scheme.
Built as a criminal cloud-hosting environment that was rented out to scammers, spammers other ne’er-do-wells, Avalanche has been a major source of cybercrime for years. In 2009, when investigators say the fraud network first opened for business, Avalanche was responsible for funneling roughly two-thirds of all phishing attacks aimed at stealing usernames and passwords for bank and e-commerce sites. By 2011, Avalanche was being heavily used by crooks to deploy banking Trojans.
The U.K.’s National Crime Agency (NCA), says the more recent Avalanche fraud network comprised up to 600 servers worldwide and was used to host as many as 800,000 web domains at a time.
“Cyber criminals rented the servers and through them launched and managed digital fraud campaigns, sending emails in bulk to infect computers with malware, ransomware and other malicious software that would steal users’ bank details and other personal data,” the NCA said in a statement released today on the takedown. The criminals used the stolen information for fraud or extortion. At its peak 17 different types of malware were hosted by the network, including major strains with names such as goznym, urlzone, pandabanker and loosemailsniffer.At least 500,000 computers around the world were infected and controlled by the Avalanche system on any given day.”
The Avalanche network was especially resilient because it relied on a hosting method known as fast-flux, a kind of round-robin technique that lets botnets hide phishing and malware delivery sites behind an ever-changing network of compromised systems acting as proxies.
“The complex setup of the Avalanche network was popular amongst cybercriminals, because of the double fast flux technique offering enhanced resilience to takedowns and law enforcement action,” Europol said in its statement.
It’s worth noting here that Avalanche has for many years been heavily favored by crime gangs to deploy Zeus and SpyEye malware variants involved in cleaning out bank accounts for a large number of small to mid-sized businesses. These attacks relied heavily on so-called “money mules,” people willingly or unwittingly recruited into helping fraudsters launder stolen funds.
At the time of the takedown, the Avalanche cybercrime infrastructure spanned more than 180 countries, according to The Shadowserver Foundation, a nonprofit group that helped authorities gain control over the Avalanche domains. Read more on Shadowserver’s role in this effort here.

Source