Shares of Equifax dropped another 4% today, including after-hours, to
$92.70. They’re now down 35%, or $50, from the happier era that ended
at 5pm EST on September 7, with the confession that it had found out six
weeks earlier that the most crucial personal data – “primarily names,
Social Security numbers, birth dates, addresses and, in some instances,
driver’s license numbers” – of 143 million consumers had been stolen.
This was promptly followed by chaos and egregious missteps, such as trying to profit from its victims. So far, at 120.4 million shares outstanding as of June 30, the six trading days have cost investors $6 billion. No one cares about consumers. They’re just the product. But $6 billion matter.
Now heads are rolling. Oh no, not CEO Richard Smith. He is not leaving the company to spend more time with his family. Instead, Equifax announced Friday evening that it sacked two lower level executives. I mean, not sacked. Chief information officer, David Webb, and chief security officer, Susan Mauldin, “are retiring,” it said, “effective immediately.”
And they had it coming.
Much was made of Mauldin’s degrees in music. But for a person her age, and with as much corporate experience as she had, college is irrelevant. Gates, Jobs, and Zuckerberg didn’t even graduate from college. What matters is how they perform their work.
And they failed to patch a vulnerability in Apache Struts, an open-source and therefore free software. The vulnerability had been “identified in early March” but wasn’t patched. The hack occurred from May 13 through July 30, 2017.
According to Equifax Friday evening:
The attack vector used in this incident occurred through a vulnerability in Apache Struts (CVE-2017-5638), an open-source application framework that supports the Equifax online dispute portal web application.
Equifax’s Security organization was aware of this vulnerability at that time, and took efforts to identify and to patch any vulnerable systems in the company’s IT infrastructure.
While Equifax fully understands the intense focus on patching efforts, the company’s review of the facts is still ongoing.
ArsTechnica was a little clearer:
The flaw in the Apache Struts framework was fixed on March 6. Three days later, the bug was already under mass attack by hackers who were exploiting the flaw to install rogue applications on Web servers. Five days after that, the exploits showed few signs of letting up. Equifax has said the breach on its site occurred in mid-May, more than two months after the flaw came to light and a patch was available.
After this software fiasco, two other people were promoted into those slots, both from within Equifax’s vaunted IT operations, now best known for not patching their Apache Struts software. The statement:
Mark Rohrwasser has been appointed interim Chief Information Officer. Mr. Rohrwasser joined Equifax in 2016 and has led Equifax’s International IT operations since that time.
Russ Ayres has been appointed interim Chief Security Officer. Mr. Ayres most recently served as a Vice President in the IT organization at Equifax. He will report directly to the Chief Information Officer.
The statement also said that the company “is fully committed to proactively supporting consumers who may have been impacted by the cybersecurity incident.”
Yup. So a day or two ago, Equifax changed its page for initiating a “security freeze” to make it a lot harder for consumers to get a security freeze (aka credit freeze).
Credit bureaus are required to offer a security freeze. But they’re not required to make it easy. Credit bureaus sell consumer data to other companies. When you try to open an account at a bank or credit card company, that company will check your credit worthiness via the data obtained from credit bureaus. If someone obtains your data that was stolen from Equifax, he can open an account in your name and borrow money in your name, and you get to fend off the creditors when they chase after their money, and your credit will be ruined too.
Identity theft is a nightmare to resolve. The best prevention is putting a security freeze at the three major credit bureaus: Equifax, TransUnion, and Experian.
A credit freeze makes this form of identity theft nearly impossible because banks and credit card companies that cannot verify the applicant’s credit history will not open a new account. And since your stolen data will be out there forever, you need to protect yourself for the rest of your life.
But to make it even harder to obtain a security freeze, Equifax put a huge distracting red button on the top center of the security-freeze page. It takes you to a page full of other stuff where a security freeze is mentioned only at the bottom, but without link.
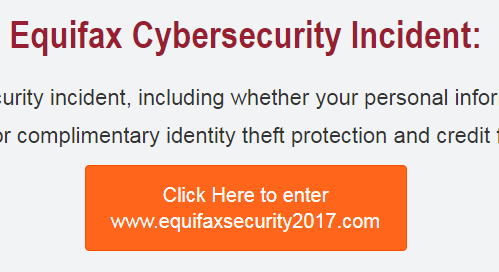 Instead, scroll past the devious red button. Now the security-freeze
section appears that used to be at the top. And it provides the appropriate link. But most people will never see it because they were deceived by the devious red button.
Instead, scroll past the devious red button. Now the security-freeze
section appears that used to be at the top. And it provides the appropriate link. But most people will never see it because they were deceived by the devious red button.
Under withering pressure and allegations of profiteering from its victims’ plight, Equifax announced that credit freezes will be free until November 21, and that consumers who paid for it starting at 5pm EST on September 7 will receive a refund.
TransUnion has become even more devious in trying to prevent consumers from initiating a security freeze and denting its revenues. Its old credit-freeze page that I’d linked in my September 7 article — and that subsequently major media outlets and State Attorneys General linked in their communications – was changed a couple of days ago.
Now that page goes through all kinds of blah-blah-blah. You have to scroll all the way down to get to the very last paragraph to find the first mention of a “credit freeze” and the new link where you can initiate the credit freeze. But even on that “credit-freeze2” page, TransUnion is trying to talk you into a “security lock” instead.
Experian has not yet changed its security freeze page.
This deviousness is a sign these companies are terrified that a mass credit freeze will hit their revenues and shares. And this isn’t a short-term blip. This is for life.
Banks, credit card companies, and other Equifax customers squeal. Consumers (the product) squeal. Congress squeals. Investors squeal. Read… The Crushing of Equifax
Source
This was promptly followed by chaos and egregious missteps, such as trying to profit from its victims. So far, at 120.4 million shares outstanding as of June 30, the six trading days have cost investors $6 billion. No one cares about consumers. They’re just the product. But $6 billion matter.
Now heads are rolling. Oh no, not CEO Richard Smith. He is not leaving the company to spend more time with his family. Instead, Equifax announced Friday evening that it sacked two lower level executives. I mean, not sacked. Chief information officer, David Webb, and chief security officer, Susan Mauldin, “are retiring,” it said, “effective immediately.”
And they had it coming.
Much was made of Mauldin’s degrees in music. But for a person her age, and with as much corporate experience as she had, college is irrelevant. Gates, Jobs, and Zuckerberg didn’t even graduate from college. What matters is how they perform their work.
And they failed to patch a vulnerability in Apache Struts, an open-source and therefore free software. The vulnerability had been “identified in early March” but wasn’t patched. The hack occurred from May 13 through July 30, 2017.
According to Equifax Friday evening:
The attack vector used in this incident occurred through a vulnerability in Apache Struts (CVE-2017-5638), an open-source application framework that supports the Equifax online dispute portal web application.
Equifax’s Security organization was aware of this vulnerability at that time, and took efforts to identify and to patch any vulnerable systems in the company’s IT infrastructure.
While Equifax fully understands the intense focus on patching efforts, the company’s review of the facts is still ongoing.
ArsTechnica was a little clearer:
The flaw in the Apache Struts framework was fixed on March 6. Three days later, the bug was already under mass attack by hackers who were exploiting the flaw to install rogue applications on Web servers. Five days after that, the exploits showed few signs of letting up. Equifax has said the breach on its site occurred in mid-May, more than two months after the flaw came to light and a patch was available.
After this software fiasco, two other people were promoted into those slots, both from within Equifax’s vaunted IT operations, now best known for not patching their Apache Struts software. The statement:
Mark Rohrwasser has been appointed interim Chief Information Officer. Mr. Rohrwasser joined Equifax in 2016 and has led Equifax’s International IT operations since that time.
Russ Ayres has been appointed interim Chief Security Officer. Mr. Ayres most recently served as a Vice President in the IT organization at Equifax. He will report directly to the Chief Information Officer.
The statement also said that the company “is fully committed to proactively supporting consumers who may have been impacted by the cybersecurity incident.”
Yup. So a day or two ago, Equifax changed its page for initiating a “security freeze” to make it a lot harder for consumers to get a security freeze (aka credit freeze).
Credit bureaus are required to offer a security freeze. But they’re not required to make it easy. Credit bureaus sell consumer data to other companies. When you try to open an account at a bank or credit card company, that company will check your credit worthiness via the data obtained from credit bureaus. If someone obtains your data that was stolen from Equifax, he can open an account in your name and borrow money in your name, and you get to fend off the creditors when they chase after their money, and your credit will be ruined too.
Identity theft is a nightmare to resolve. The best prevention is putting a security freeze at the three major credit bureaus: Equifax, TransUnion, and Experian.
A credit freeze makes this form of identity theft nearly impossible because banks and credit card companies that cannot verify the applicant’s credit history will not open a new account. And since your stolen data will be out there forever, you need to protect yourself for the rest of your life.
But to make it even harder to obtain a security freeze, Equifax put a huge distracting red button on the top center of the security-freeze page. It takes you to a page full of other stuff where a security freeze is mentioned only at the bottom, but without link.
This is what the devious button looks like that you do not want to click:

Under withering pressure and allegations of profiteering from its victims’ plight, Equifax announced that credit freezes will be free until November 21, and that consumers who paid for it starting at 5pm EST on September 7 will receive a refund.
TransUnion has become even more devious in trying to prevent consumers from initiating a security freeze and denting its revenues. Its old credit-freeze page that I’d linked in my September 7 article — and that subsequently major media outlets and State Attorneys General linked in their communications – was changed a couple of days ago.
Now that page goes through all kinds of blah-blah-blah. You have to scroll all the way down to get to the very last paragraph to find the first mention of a “credit freeze” and the new link where you can initiate the credit freeze. But even on that “credit-freeze2” page, TransUnion is trying to talk you into a “security lock” instead.
Experian has not yet changed its security freeze page.
This deviousness is a sign these companies are terrified that a mass credit freeze will hit their revenues and shares. And this isn’t a short-term blip. This is for life.
Banks, credit card companies, and other Equifax customers squeal. Consumers (the product) squeal. Congress squeals. Investors squeal. Read… The Crushing of Equifax
Source