
Acer, Dell, Fujitsu, HP, Lenovo, and Panasonic have officially confirmed that products incorporating Intel chipsets are affected by eight security flaws that allow hackers to take over devices.
Intel published details about these flaws in a security advisory, on Monday. The eight bugs affected core Intel CPU technologies such as the Intel Management Engine (ME), Intel Server Platform Services (SPS), and Intel Trusted Execution Engine (TXE).
Intel had deployed these technologies in Intel products such as:
6th, 7th & 8th Generation Intel® Core™ Processor Family
Intel® Xeon® Processor E3-1200 v5 & v6 Product Family
Intel® Xeon® Processor Scalable Family
Intel® Xeon® Processor W Family
Intel® Atom® C3000 Processor Family
Apollo Lake Intel® Atom Processor E3900 series
Apollo Lake Intel® Pentium™
Celeron™ N and J series Processors
Only the products using the following firmware versions were affected:
ME firmware versions 11.0/11.5/11.6/11.7/11.10/11.20
SPS Firmware version 4.0
TXE version 3.0
Many PC and notebook vendors incorporated these CPUs running vulnerable firmware versions in server, desktop, and notebook models they sold to users across the world.
At the time Intel published its advisory, it was not clear what vendors deployed the vulnerable firmware versions with Intel-based desktops and laptops.
Over 900 of PC and laptop models affected
As the week progressed, new information has come to light. The following vendors have published lists of products that use Intel products running a vulnerable firmware.Not all vendors have released patches, and users should revisit those pages to download firmware updates for their devices when available.
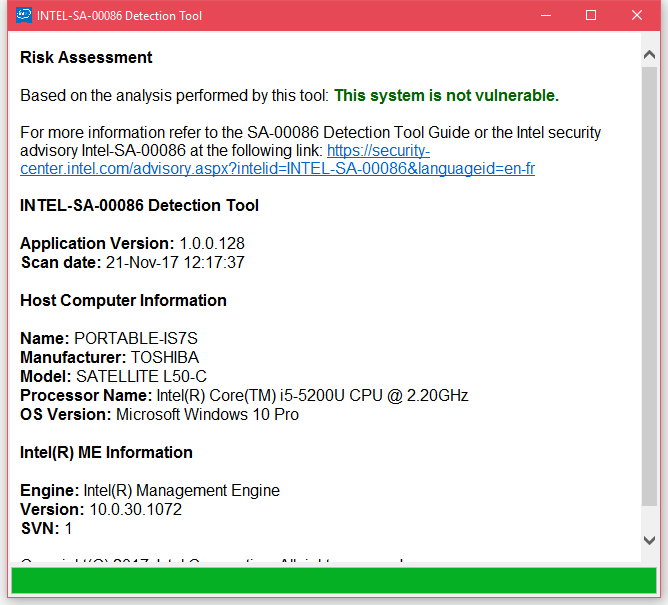
If you don't spot the server, desktop, or laptop vendor and model in these pages, Intel has also released a Windows and Linux tool that scans the user's PC and tells him if he's impacted by the recently disclosed bugs. On Windows, users should run the Intel-SA-00086-GUI.exe file to view scan results (image below).
- Impersonate the ME/SPS/TXE, thereby impacting local security feature attestation validity.
- Load and execute arbitrary code outside the visibility of the user and operating system.
- Cause a system crash or system instability.